Blog
Understanding the Basics of a Secure Code Review
Code analysis methodology is a comprehensive process that involves examining the source code of an application to identify issues that could potentially affect its security, performance, and maintainability. By using specialized tools that automate the process of examining the code, identifying potential issues, and providing feedback to the developers, code analysis methodology plays an essential role in software development.
As Application Functionality Grows, Breaches Skyrocket
It is difficult to estimate the exact number of applications that are vulnerable to breaches, as it depends on various factors such as the security measures implemented, the types of vulnerabilities present, and the sophistication of potential attackers; however, it is generally recognized that the majority of applications have at least some vulnerabilities that could potentially be exploited by attackers. According to a recent report 76% of applications have at least one security flaw, and 24% have at least one high-severity flaw.
Why Application Security Matters: A Developer's Guide
Application security matters because it helps protect sensitive data, maintain the privacy and integrity of systems, and prevent unauthorized access and exploitation of vulnerabilities. All of these issues can lead to financial loss, reputational damage, and loss of trust. Ensuring the security of applications is crucial for businesses, organizations, and individuals to secure their assets and meet legal and regulatory compliance requirements.
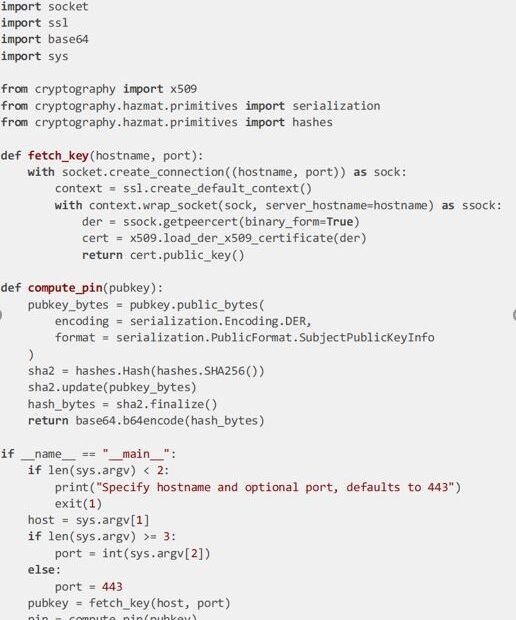
Was That Key Copied
By Jonathan Landis Practice Director and CISO Certificate management takes work. It takes less work if you are using the ACME protocol with something like Certbot from the Let’s Encrypt
Security for Enterprise Transitions
Jon Espenschied, CISO Mergers, acquisitions, material incidents, and exits After going through several corporate mergers as a passenger or minor contributor, it was a privilege to be “on the inside
Audits Without Surprises
A formal security or privacy audit may be motivated by a business requirement, state or federal regulation, or a proactive initiative to manage risk for your company. Regardless of the
Information Security Consulting Services
I’m not going to lie, I love Yoo-hoo drinks, to the point that I have at least one a day and get grumpy if I don’t have one available when
Reviewing Information Security Access Control Strategy
Often in security we get so caught up in firewall rules, anti-virus alerts, or answering audit and compliance surveys that we sometimes put the cart before the horse. We focus
Being an Aware Information Security Leader
I’m an avid hiker and have been a youth leader in several organizations over the past 20 years or so. In outdoor leadership, a core component of leadership is awareness:
Secure E-voting by Another Name: Vote-by-Mail
A data-security perspective on why casting a ballot by mail is more secure than voting in person, and how the Washington State system has potential to be even stronger 2020
The Rocky Road to Success with the Frida Tool
Frida, the code instrumentation toolkit, is excellent software. It gives you the power to observe and tamper with the memory of a running process by hooking functions and changing parameter
Working with X-Frame-Options and CSP Frame-Ancestors
Have you heard of the Content Security Policy (CSP) “frame-ancestors” directive? It is a newer alternative to the X-Frame-Options header, which offers better control and broad, but not universal, browser
NIST Cybersecurity Metrics
Metrics are a passion of us at Caliber Security. They provide answers to key questions:• Should we invest more or less in security?• Are we meeting commitments?• Which groups are
Why Information Security Penetration Testing is Important
Every organization that comes to us for penetration testing is driven by different motives. Our clients come from a variety of industries and range from enterprise level organizations down to